Upon opening the .pcap file, the first thing I do is inspect the protocols used in the sample.
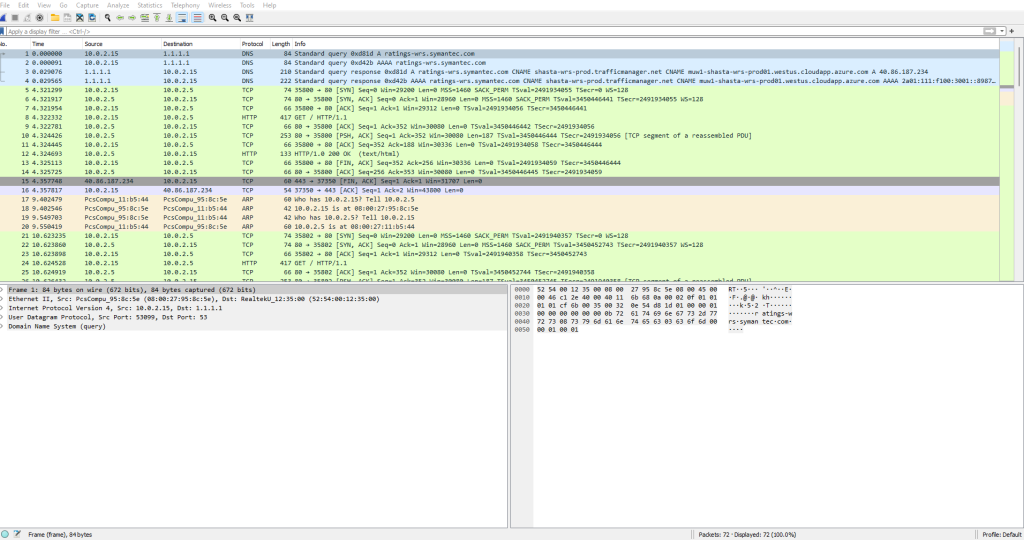
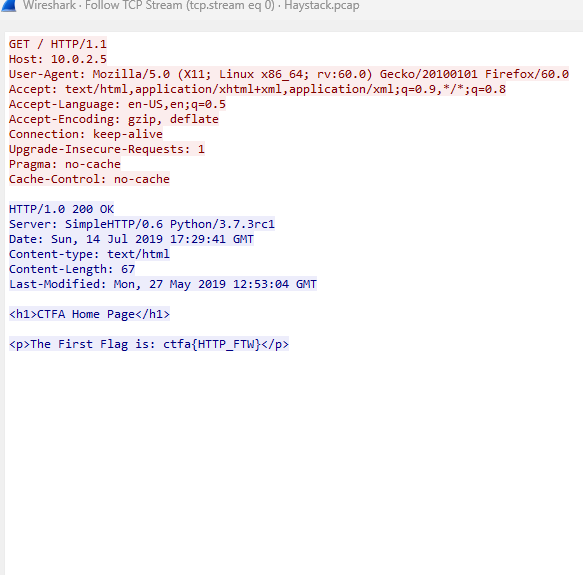
I knew that the flag came from a website, so I have a good idea as to where I should look first. I begin with the HTTP packets, and start to analyze them one at a time. Sure enough, I was able to find the first flag in text/html packet transmitted over HTTP.
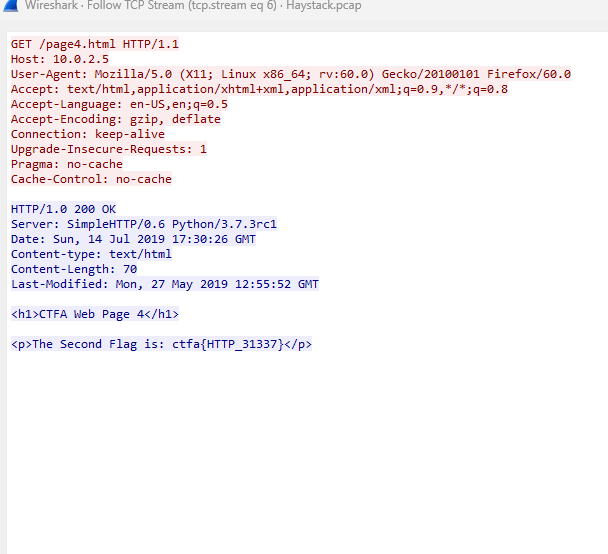
However, there is a second flag that needs to be obtained from the file.
Because I found the first flag in a HTTP packet, I figured that I might as well continue to look through the text/html packets one by one. I’m able to sort these packets by protocol to narrow the search down.
By following the TCP stream, similar to the first packet, I was able to identify the second flag.
By narrowing down the scope of the packets by including overall context, I was able to find the flags and accurately present them back.