In December 2013, Target suffered the worst customer data breach from a retail store in history. The cyber attack resulted in the compromise of over 40 million credit card records and 70 million customer records. As a result of the attack, the attack ended up costing Target over $200 million.
The attack was a significant blow to the trust that customers had in their payment data being secure. And surprisingly, it could have been much worse.
How It Happened
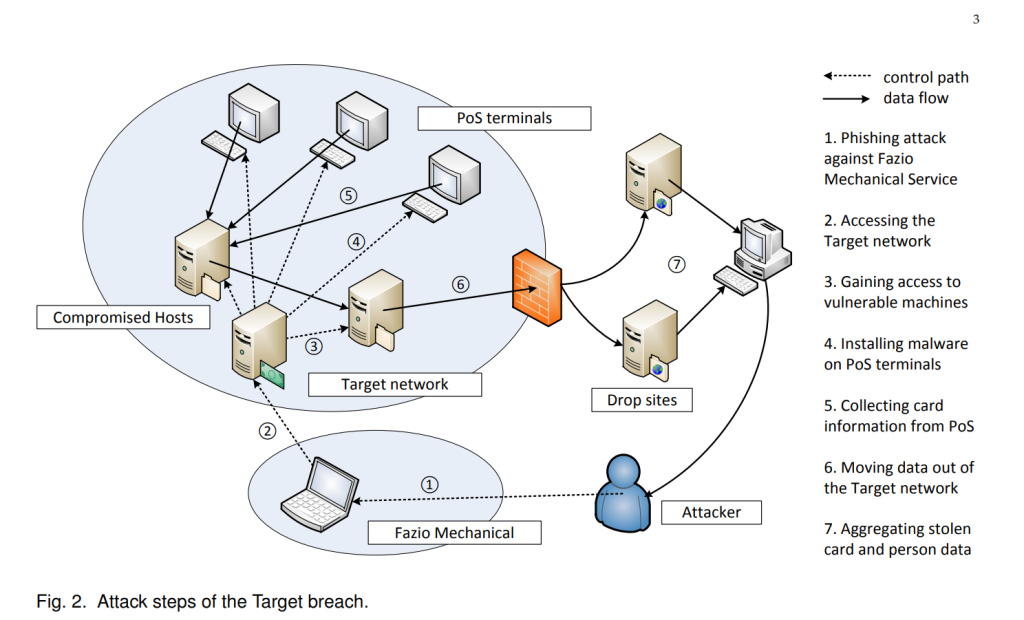
Despite being an incredibly costly hack, it was not as sophisticated as one would think. In September 2013, a heating and air conditioning company called Fazio Mechanical Services suffered a security breach. Fazio Mechanical Services worked with Target and had access to Target’s external billing system through a vendor portal. The Russian cybercriminals were able to gain access to the vendor portal through a social engineering attack on one of their employees.
Once the social engineering attack succeeded, a trojan program was installed onto a company computer. This trojan gave hackers full access to a system by taking control of the employee’s credentials.
Once the attackers had gained access to the vendor portal, the hackers moved through Target’s network to then gain access to their Point of Sale system through a Windows file server. The server was then infected, and attackers were now able to control the actions of the file server.
A BlackPOS malware program was then installed into the POS system. This would give access to the hackers to record all credit card information that was being processed by scraping the RAM from the POS system. Most of Target’s POS systems were infected with this malware as a result of the breach.
Once the BlackPOS malware successfully gathered the credit card information, it was exported to the infected Windows file server. The Windows file server would then ping the hacker’s external file server, and then sent the credit card data using FTP (file transfer protocol).
Were there warning signs?
Yes. But Target’s network administrators were not willing to act on the information that they were given that clearly showed that a data breach was occurring.
On November 15, attackers were able to gain access to Target’s network, and less than two weeks later were able to send the BlackPOS malware program to most POS systems. Six months before the breach, Target installed a malware detection service called FireEye onto their network. FireEye alerted network administrators on November 30 that a malware program had been detected on their internal network. However, the alerts were dismissed and the auto functions were turned off.
Shockingly, the FireEye program that was installed on Target’s network had a feature that would give it the ability to automatically shut down any malware program that had been detected. However, Target’s network administrators had turned the program off to give more configuration ease. Had this feature been enabled, it could have prevented an unknown amount of data from being exported to the hacker’s server.
On December 2, hackers were able to successfully export the credit card and customer data to their file server. Again, FireEye alerted that a breach was occurring. On December 12, 2013, the Department of Justice notified Target of the breach, and three days later were able to remove the malware from the POS systems.
What could have been done?
Even though Target did have enough foresight to install malware detection software onto their network, there were key openings that were not considered when the hardening process of Target’s networks occurred. By allowing third parties to gain access to their network through a network portal, they relied on other companies’ security policies to protect against their internal services. While Target was not responsible for the Fazio Mechanical Services breach, they were responsible for allowing third-party vendors to gain access to their network without creating proper mechanisms.
Companies that must give access to their internal network should be especially careful of allowing these networks to access areas of the network that contain private data. Target’s network policy went against the PCI DSS (Payment Card Industry Data Security Standard), and the network administrators should have instituted a policy to prevent this from happening.
Target should have also instituted a proper escalation process that would have ensured a proper response to the FireEye alerts. Whoever was monitoring Target’s network should have been able to alert the proper leaders to what was going on, instead of ignoring the problem.
What can we learn?
Target’s data breach showcases the importance of understanding a network’s security posture. Preparing for the worst-case scenario would have helped prevent this data breach, and shows us that a security system is only as strong as its weakest link. If there had been a better understanding of Target’s security posture, proper measures could have been put into place to prevent this type of breach from occurring.