It’s incredibly uncommon to find any email services that offer unencrypted email services. Gmail, Outlook, and Yahoo all provide in-transit encryption, and many services offer at-rest encryption add-ons for these services as well. However, there are occasional circumstances where the lack of at-rest encryption can be exploited through client-related hacks. In 2019, Microsoft’s Outlook client was hacked, allowing cybercriminals to access many users’ email content.
The lack of encrypted emails can be especially concerning for small business owners. SiteLock data from 2018 shows that over 70% of cyberattacks target small to medium-sized businesses. Data breaches for small businesses can be detrimental and can end up causing irreparable damage to a business’s reputation and competitive advantage.
To investigate the vulnerability of unencrypted emails, I utilized the protocol analyzer Wireshark to see how easy it is to view unencrypted emails.
To run send an unencrypted email using SMTP, I entered the following command into a Linux terminal using the “mailutils” package:
echo "The secret password is: pumpkins" | mail -s "Secret Password" calebmartinez123456789@gmail.comUsing Wireshark and following the TCP stream, I was able to see find the following packet in clear, unencrypted text:
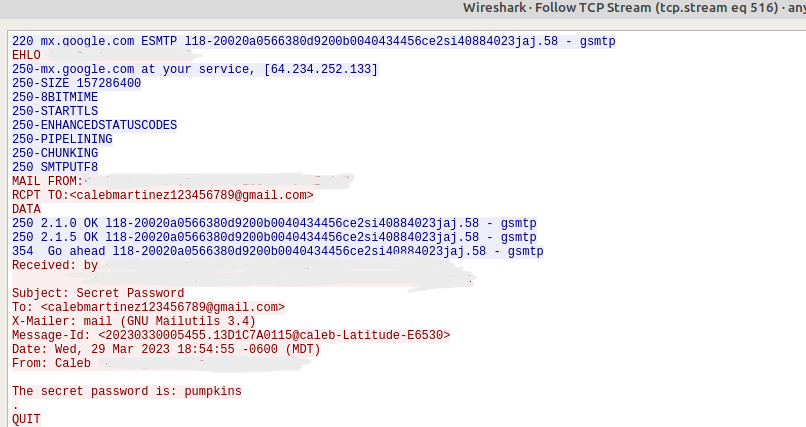
As we can see, the email is entirely visible in plain text. “The secret password is: pumpkins” is clearly readable. Anyone who has a protocol analyzer would be able to read the contents of this email.
Now, to contrast, let’s inspect the contents of what would be an encrypted email. Here are the plain text findings of what would be an encrypted email sent over the same network:

Without the encryption key, the contents of the email would be incredibly difficult to discover.
When we compare the two versions of email transportation methods, it’s clear that it would the more what the more secure option is. However, encryption over the network does not mean the email is safe from all snooping. If the email service does not provide end-to-end encryption (a service provided by Proton Mail, for example) the contents of the email could be vulnerable once the email leaves the transport-level encryption service included by providers Google, Microsoft, and Yahoo.
Does this mean that everyone who uses these services should panic? Not necessarily, but it would be in their best interest to at least be aware of the risks created when using unencrypted email.